
How to Use bundler-audit to Keep Your App's Dependencies secure
These days, maintaining a secure codebase is crucial. Vulnerabilities in your application’s dependencies can pose significant risks to the security of your application. This is where tools like bundler-audit come into play. bundler-audit is a gem that helps you identify and manage security vulnerabilities in your Rails application’s external dependencies. In this article, we will explore how to use bundler-audit to keep your Rails codebase secure.
What is bundler-audit?
bundler-audit is a command-line tool that scans your Rails project’s Gemfile.lock and checks for known security vulnerabilities in your application’s gems. It leverages the Ruby Advisory Database to provide up-to-date information about vulnerabilities in your gem dependencies.
Getting started with bundler-audit
To get started, you need to install bundler-audit by running the following command: gem install bundler-audit.
You can run bundler-audit to get a list of all the vulnerabilities in your application. There are many different flags that you can use to change the output you get from bundle-audit, including ignoring specific advisories, checking a custom Gemfile.lock, and outputting the results to JSON, etc.
To maintain a secure codebase continuously, consider automating bundler-audit scans as part of your development and deployment processes. You can integrate bundler-audit with your CI/CD pipeline to ensure that vulnerabilities are detected and addressed at every stage of development.
How to read your results
bundler-audit will analyze your Gemfile.lock and compare it against the Ruby Advisory Database mentioned above. It will display a list of any identified vulnerabilities along with their details:
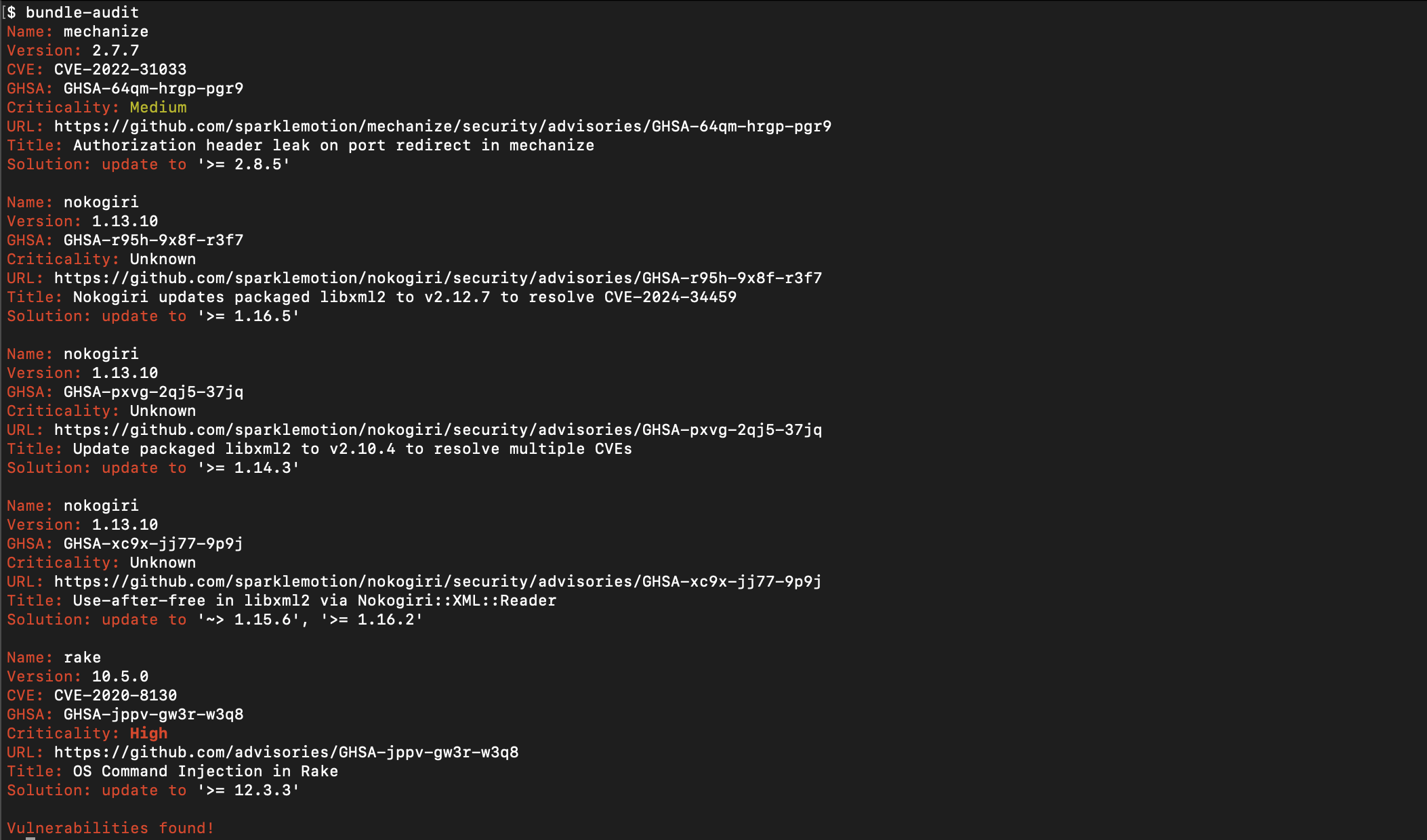
Here’s an explanation of what these above elements mean:
- Version - The version of the vulnerable gem found in the
Gemfile.lock. - CVE - This is a reference to the CVE entry. CVE stands for the Common Vulnerabilities and Exposures (CVE) , a system created by The United States’ National Cybersecurity FFRDC that contains information about publicly known information-security vulnerabilities and exposures. Every CVE entry is assigned a unique identifier to help users to discuss, track, and address vulnerabilities without ambiguity.
- GHSA - This is a reference to the GHSA entry. GitHub has it’s own security vulnerability database containing information about vulnerabilities in projects hosted on GitHub.
- Criticality - This is the severity level of the vulnerability. A vulnerability can have one of several severities from ‘Low’ to ‘Critical’.
Fixing Vulnerabilities
Identifying vulnerabilities is just the first step. To enhance your Rails application’s security, you must address and fix vulnerabilities promptly. Here’s how you can do that:
- Determine if there are updated versions of the vulnerable gems available. You can find this information on the RubyGems website or by checking the gem’s GitHub repository.
- Once you identify an updated version of the gem, update your
Gemfileto specify the new version. - After updating your Gemfile, run
bundle update vulnerable_gemto update the gem to the latest version. I like to add the--conservativeflag to ensure I am not updating any unnecessary dependencies. - After updating your gems, re-run
bundle-auditto ensure that you’ve addressed all vulnerabilities. If there are no more vulnerabilities reported, you’ve successfully secured your application.
Conclusion
Security should always be a top priority. bundler-audit is a valuable tool that simplifies the process of identifying and addressing vulnerabilities in your application’s gem dependencies. By regularly scanning your codebase and taking prompt action to fix vulnerabilities, you can enhance the security of your Rails application and protect it from potential threats. Remember that security is an ongoing process, and staying vigilant is key to maintaining a secure codebase.
Need help keeping your Rails applications secure? Contact us for a security audit!